Process Methodology for Cybersecurity
A research methodology explains and discuss data or information collected that is used on the research is a key part for any thesis or presentation (Scribbr, 2019), therefore a Process Methodology is used to understand the previous process to accomplish tasks in Cybersecurity, will be shown on the chart below the series of steps to follow in a specific order.
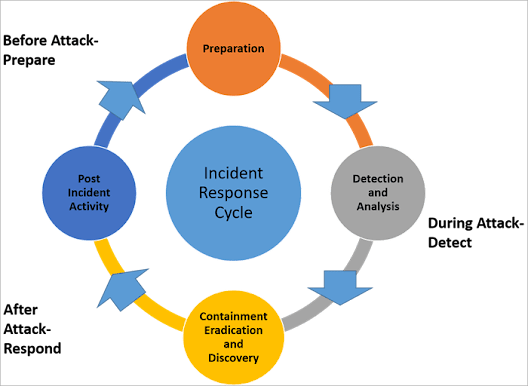
(Source: Softwaretestinghelp, 2023)
To have an effective manage of security there are six steps to follow, these should be follow for an specific team responsible for incidents. The followint steps are:
- Preparation: Important part that is responsible to provide valid information to the CSIRT (Computer Security Incident Response Team) this step is important because it help to figure out assets which become critical security attention for the team.
- Detection: Second stage is more crucial than the first one because the team should be able to look for any breach or potential threat, once is detected the team must understand the nature and severity to document every action take and also understand the "when", "why" and "where" of the incident.
- Containment: When the incident is detected by the CSIRT the team must isolate the case to there will not be any further damage, could be a single and easy step or could be hard depending on the situation and the target of the threat.
- Eradication: The fourth step is more complicated for the simple reason of finding the root of the problem to take severe, strong and immediately actions.
- Recovery: The process of recovery and reinforce of the systems and resume of the production with extremely care, this stage involves critical thinking suitable for restoration.
- Post-incident follow-up: Last stage that must be completed within two weeks of the occurrence to patch any gap that were not completed before and erradicated the incident.
(Source: https://www.softwaretestinghelp.com/what-is-incident-response-plan/#Incident_Response_Cycle)
In conclusion, the implementation of cybersecurity on a real scenario must follow the previous steps to ensure an effective managing of security, that can prevent hard attacks against compannies or universities regardless information that can be leaked, because facing a cyber attack it could be just the tip of the iceberg.
References:
What is incident response plan - complete guide (2023) Software Testing Help. Available at: https://www.softwaretestinghelp.com/what-is-incident-response-plan/#Incident_Response_Cycle (Accessed: 03 June 2023).
What’s the difference between method and methodology? (no date) Scribbr. Available at: https://www.scribbr.co.uk/faqs/method-vs-methodology/ (Accessed: 03 June 2023).

Comments
Post a Comment